Research Unlock: Security Breaches in 2024: Zero Knowledge Solutions & Midnight Network

Introduction: State of Security in 2024
In 2024, security breaches across Web2 and Web3 highlighted ongoing vulnerabilities. In this report, we will shed light on a few key security incidents, affected users, and solutions which can help counter them.
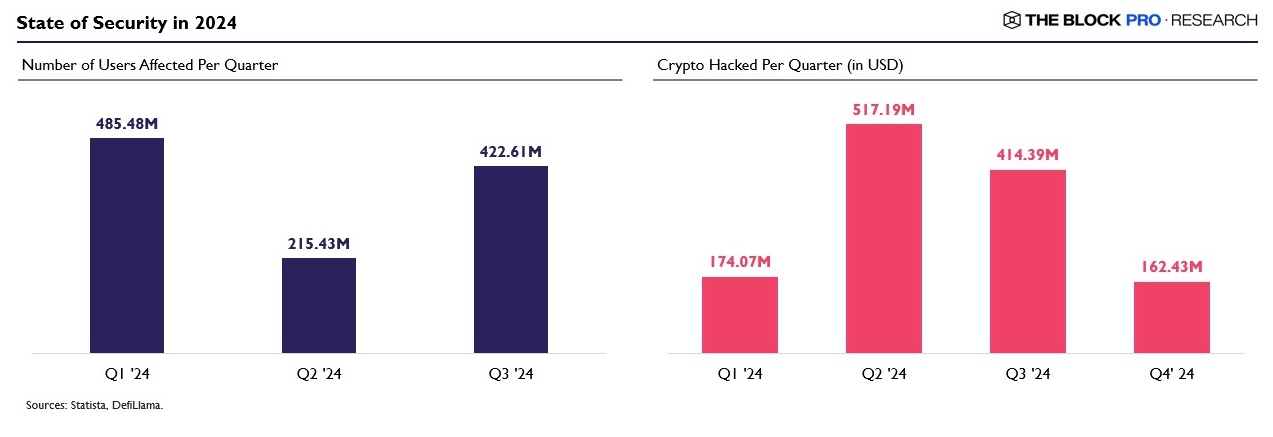
On the Web2 side, there were more than 30 thousand security incidents and 10 thousand data breaches through social engineering, software vulnerabilities, and malware according to Verizon’s 2024 Data Breach Investigations Report . The average cost of these attacks was 4.88 million dollars. This is the amount paid in ransomware and the value lost due to downtime. These data breaches impacted 1.12 billion users worldwide in just the first three quarters of the year.
As for Web3, a total of 1.26 billion dollars has been lost to hacks this year alone. The attacks were primarily due to poor smart contract logic, lack of validation and checks, poor infrastructure and private key management.
Overall, 2024 was a significant year in terms of data breaches and value hacked. These vulnerabilities and security breaches show us that there is a lot of room for improvements when it comes to security and data protection within the space.
As the need for secure and privacy-preserving solutions grows, IOG is developing the Midnight network , a new generation blockchain focused on data protection with features that can enable cookieless environments and selective data disclosure. Midnight is a partner chain to the Cardano blockchain that leverages Zero-Knowledge Proofs (ZKPs) to ensure secure transactions that protect users’ data and shield metadata from nefarious actors.
Security Challenges: Web2 and Web3 environments
Web2 and Web3 ecosystems face many different threats, including software vulnerabilities, social engineering attacks, human errors, and more. In this section, we will explore these security challenges and examine how such attacks can compromise the integrity of these systems.
Web2
Phishing Attacks
Phishing attacks occur when attackers deceive users into revealing sensitive information such as login credentials or financial details. These attacks are often carried out through fraudulent emails, messages, or websites that mimic trusted entities. For example, an attacker might send an email pretending to be from a bank, directing users to a fake website that collects their account details.
Man-in-the-Middle (MITM) Attack
MITM attacks happen when attackers intercept and potentially alter communication between two parties without their knowledge. This often occurs on unsecured or poorly encrypted networks, allowing attackers to steal sensitive information such as login credentials, financial data, or private messages.
SQL Injection
SQL injection is a technique where attackers inject malicious SQL code to manipulate a database and gain unauthorized access to a system. Attackers often use SQL commands combined with logical operators, such as OR and AND, to exploit vulnerabilities in the application’s input fields. For example, attackers can craft queries that are always evaluated as true, tricking the system into granting access to restricted areas or sensitive data.
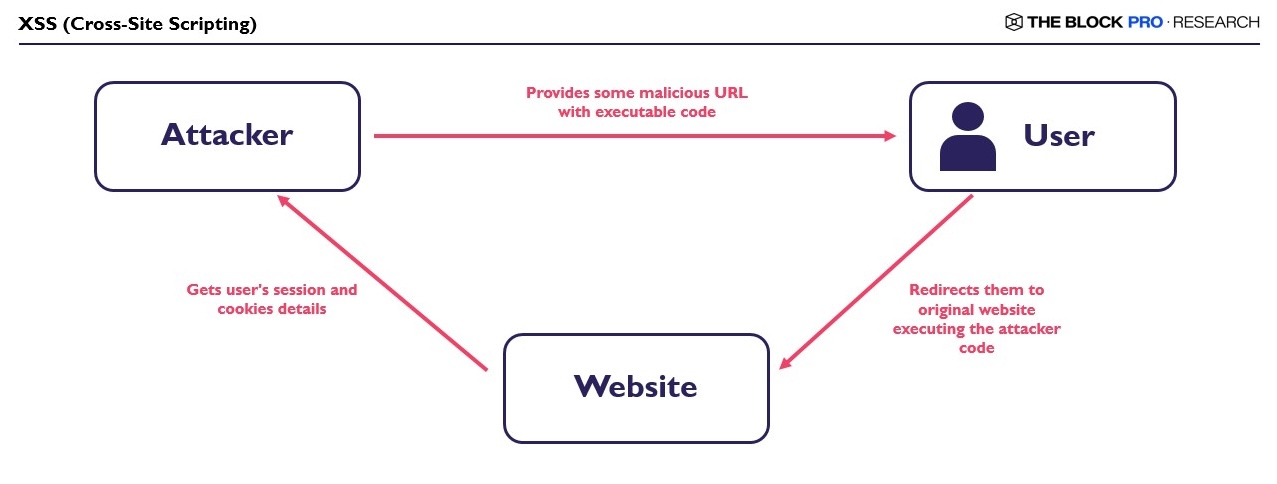
XSS (Cross-Site Scripting)
Cross Site Scripting occurs when a user clicks on a malicious URL executing malicious code on their device, therefore providing session details, cookies, and private information to an attacker, which can then be used to authenticate on any website.
IDOR (Insecure Direct Object References)
This is a classic mistake which references objects in the user’s system based on their input. This can lead to malicious input being processed by the system, therefore exposing private information. This could be user info or any file stored in the server.
CSRF (Cross-Site Request Forgery)
Cross-Site Request Forgery occurs when there is no CSRF token attached to the URL authenticating whether a request is legitimate, letting an attacker perform an action on behalf of the user. This can include bank transfers or any other malicious activity.
Sensitive Information Exposure
Users' passwords and private information like credit card details should be hashed on the server side by algorithms like SHA-256 or RSA. If neglected, this can make a user vulnerable to attacks and data leaks.
Malware Attack
Malware attacks involve malicious software designed to disrupt, damage, or gain unauthorized access to systems. This can include ransomware, which locks users out of their files until a ransom is paid, or spyware, which silently gathers sensitive information. Malware is often delivered through email attachments, malicious links, or infected downloads.
Security Misconfiguration
Security Misconfiguration vulnerabilities arise from improper or incomplete configuration of applications, which can include issues such as exposing sensitive domains, running outdated software with known vulnerabilities, enabling unnecessary services, revealing stack traces, and other misconfigurations that can be exploited by attackers.
Web3
Input Validation
Input validation should be handled at the smart contract level to ensure that user-provided inputs do not lead to unexpected behavior. Failure to validate inputs can expose vulnerabilities, enabling exploits such as fund theft, inflated gas costs, or denial-of-service (DoS) attacks that render the contract unresponsive. For instance, neglecting to validate numerical inputs may allow an attacker to trigger overflow or underflow errors, causing disruptions in the contract’s functionality and logic.
Mathematical Errors
Mathematical errors refer to any calculations performed at the smart contract level, including the use of token balances, which may result in returning more value to a user/attacker than anticipated. Since Solidity doesn’t natively support decimals, rounding errors may occur, leading to unintended financial consequences. Improper handling of floating-point arithmetic can lead to significant losses. To address this, developers should implement precision control techniques to ensure accurate calculations.
Oracle Manipulation
Oracle Manipulation attacks are some of the most notorious in Web3 which lead to non-intended token prices. This could originate if a protocol has an in-house oracle, uses a service which doesn’t validate prices properly, or has non-trustworthy validators or network participants. This could lead to major impacts when calculating position sizes and liquidation thresholds in the DeFi ecosystem. These manipulations can also be executed using flash loans, which can aid in artificially inflating an asset’s value, helping the attacker to manipulate DeFi protocols.
Lack of Proper Access Control
Access Control, or defining permissions based on specific roles, is important to have in any application. Improper access control can allow malicious actors to gain unintended access to execute unauthorized code. This can be done at the smart contract level where users have addresses with specific roles for executing particular contract functions - i.e. by assigning roles as modifiers to a function. It is important to not give improper access to any particular role, and multiple roles should be used to reduce a contract’s attack surface area. This way, if an EOA (Externally Owned Account) with special access is compromised, exploits can be minimized.
Reentrancy Attacks
Reentrancy Attacks occur when a contract’s function allows for external calls to be made during execution and before finalizing state updates. This allows an attacker to use the same contract state and repeat certain malicious actions like withdrawals which can drain a contract’s funds.
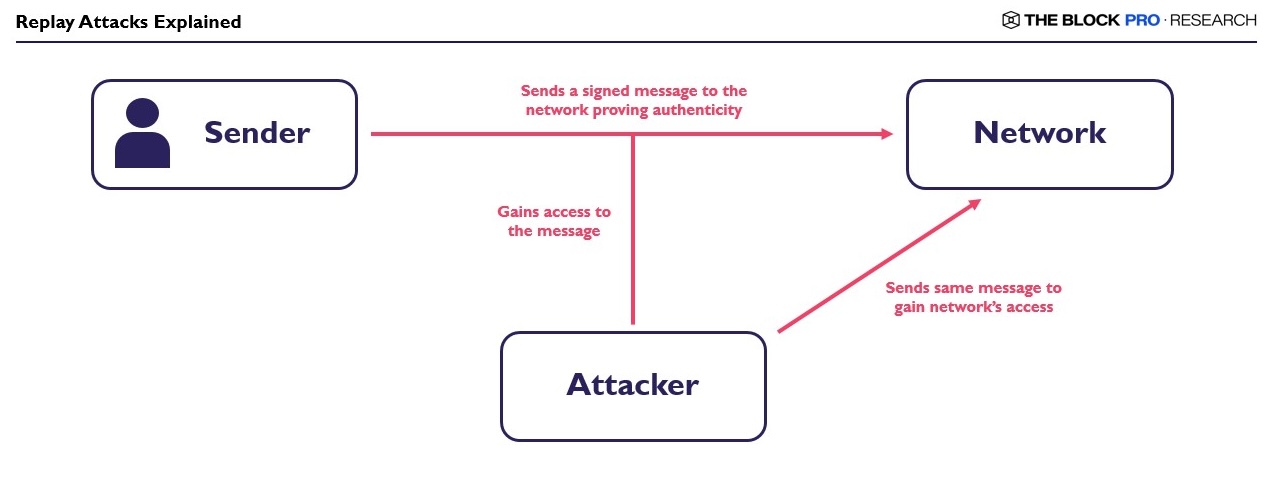
Replay Attacks
Replay Attacks occur when an attacker replays a valid transaction or action done by the actual sender. Attackers intercept or capture the message sent by the original sender and rebroadcast it to the network to gain authentication or initiate malicious actions on the network.
Frontrunning and Sandwich Attacks
Frontrunning happens when an attacker notices a transaction which can affect the price of a particular asset, and subsequently sends their transaction with a higher gas price, such that the new transaction is executed first and the frontrunner can profit off the updated price of the original sender’s transaction.
Sandwich attacks work similarly, however, are defined by a frontrunner placing a sell order immediately after the transaction that was being frontrun.
Governance Attacks
Governance attacks occur when a hacker is able to get enough voting rights to execute malicious transactions through a DAO. Attackers can do this through acquiring tokens via flash loans, in turn temporarily gaining enough power in the DAO to pass and execute a governance decision. In order to prevent this, projects typically employ strict governance frameworks that cannot be tampered with.
Case Studies: 2024 Exploits
After reviewing common security exploits prevalent in Web2 and Web3, below are a few examples of recent exploits that have targeted both ecosystems.
Web3 Exploits
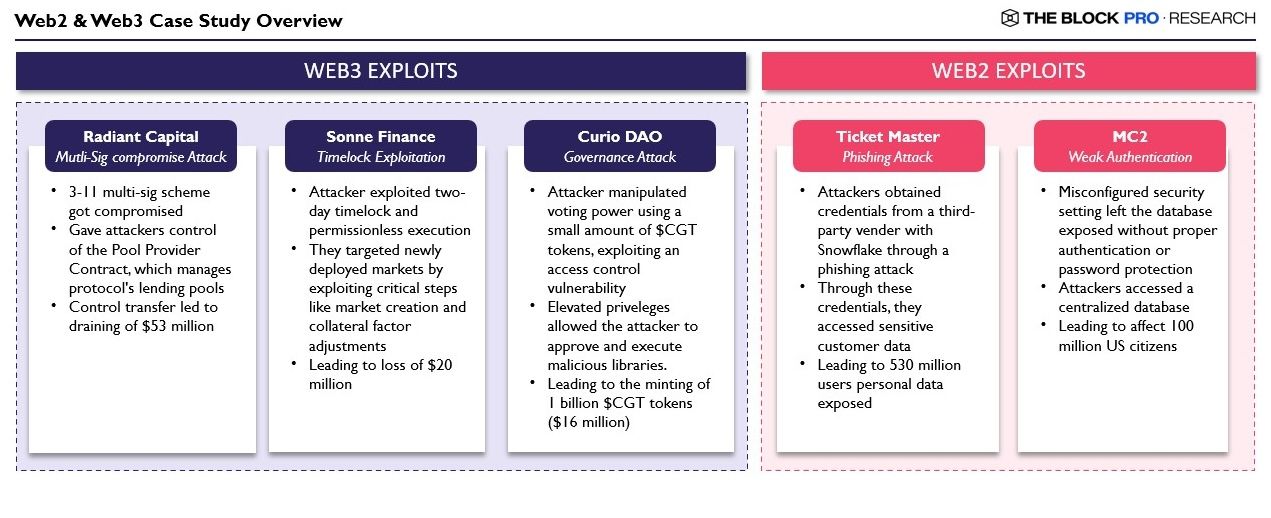
Radiant Capital
Multi-Sig Compromise Attack
Radiant Capital is an omnichain money market that suffered from two simultaneous attacks, one of which was through a flash loan. The attackers tricked signers to sign a malicious transaction, where the protocol had implemented a 3-of-11 multi-sig scheme requiring 3 key signatures to approve important transactions. The attacker used malware to show the legitimate transaction data on the frontend of Gnosis Safe Wallet which helped them to collect the legitimate signatures. Using these signatures, the attacker transferred the control of the Pool Provider Contract to themselves. The Pool Provider contract manages protocol’s various lending pools, which allowed the attackers to drain $53 million from multiple pools on multiple chains.
Sonne Finance
Timelock Exploitation
Sonne Finance, a crypto lending protocol, got drained for $20 million due to a known vulnerability associated with Compound Finance’s v2 contracts, in which attackers are able to exploit newly deployed markets. While Sonne Finance did their part by introducing timelocks and multi-step execution to prevent this, hackers were able to penetrate the protocol and execute their attack before necessary safeguards were implemented. They did the same for the VELO market, splitting critical operations like market creation and collateral factor adjustments into separate transactions. The two-day timelock allowed anyone to execute these transactions after the timelock expired. The permissionless nature of the scheduled transactions allowed the attacker to control the execution and manipulate the vulnerable market.
Curio DAO
Governance Attack
Curio is a DeFi protocol which deals in tokenized real-world assets. It got hit by a $16 million hack due to an error in their access control mechanism, enabling an attacker to mint 1 billion $CGT tokens. The attacker used a minimal amount of $CGT tokens to manipulate their voting power and elevate privileges within the smart contract. Using the elevated privileges, the attacker approved a malicious contract as an exec library via the plot function.Through a delegatecall to this library, the attacker was able to execute arbitrary actions within the Curio DAO contract, resulting in minting of unintended tokens.
Web2 Exploits
Ticketmaster
Phishing Attack
The exploit of the popular ticket sales and distribution company for concerts, sports and other events affected 560 million users worldwide. The leaked information includes users names, addresses, phone numbers, and payment details. The attack originated through Snowflake, a third party cloud database, whose compromise similarly affected dozens of other companies. The attackers got access to the credentials of a third party vendor working for Snowflake customers through a phishing attack. Using these credentials, hackers were able to bypass the security gaining access to the customers data. After gaining this data, hackers sold this data on the dark web.
MC2
Weak Authentication
MC2 provides background check services and sources data from thousands of first-party data sources which are then linked to a singular database. Around 2.7 billion records were exposed including names, date of birth, addresses, social security numbers, and phone numbers affecting around 100 million US citizens. The breach occurred when a misconfigured security setting left the database exposed without password protection.
Midnight Network’s Architecture and Exploit Mitigation
Hacks occurring this year revolved primarily around poor data management, centralized storage, improper validation, poor code logic, and social engineering. While social engineering is the most common reason for the hacks, the other attack vectors can still largely be mitigated with the utilization of enhanced security architectures. When it comes to data protection, ZK based blockchains like Midnight network ensure the user's data remains secure and private.
In this section we will shed some light on the Midnight architecture, its unique features, and how they can help mitigate such attacks.
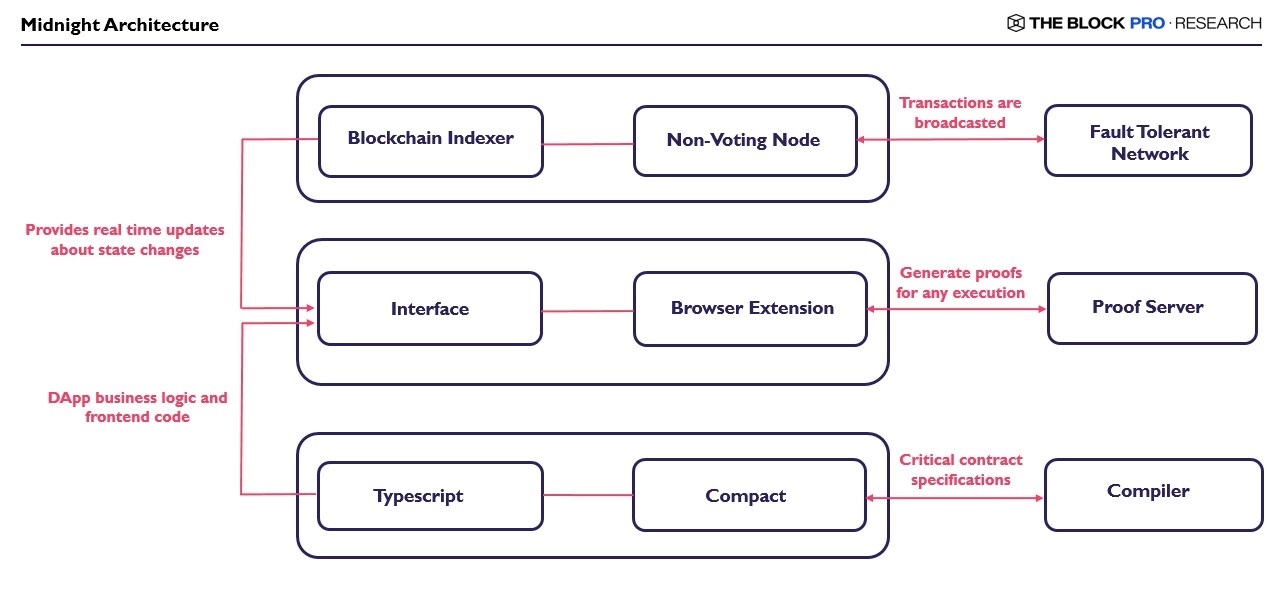
The above architecture shows different components involved in the Midnight architecture. At the base level the business logic is written in Typescript while the contract specifications are written in a Typescript-based Domain Specific Language (DSL) called Compact . The browser interface and extension handles user interaction and communicates with the proof server, which generates proofs for the state updates. The blockchain indexer and non-voting node provide real-time updates of the network, and the fault-tolerant network ensures secure transaction broadcasting and state validation. This modular architecture supports privacy, scalability, and security.
Data Shielding and Selective Disclosure
Midnight allows for transactions that don’t share user data or metadata with unintended parties. This is done through a shielded resource called DUST, which is used as gas on the network to facilitate transactions and ensure that transaction metadata is protected to prevent correlation. Moreover, personal data is encrypted and verified through ZK proofs without storing it anywhere. The proofs are generated using zk-SNARKs, an industry-leading proof system.
Another interesting feature in development is selective disclosure, which will enable the creation of user-controlled access keys that can allow very specific actors to view certain encrypted data, used for regulatory compliance and meeting business policies.
Mitigating Attacks - Data Shielding
Midnight’s data shielding mechanism ensures that user data, metadata, and transaction details are protected from exposure. By leveraging the DUST resource and relying on ZK proofs instead of the transmission of actual data, Midnight transactions protect users’ sensitive information and prevent attackers from exploiting their data.
This architecture is particularly effective for scenarios involving personally identifiable information (PII), as seen in hacks like Ticketmaster and MC2, where users' personal data were leaked.
Additionally, selective disclosure will enable controlled access to encrypted data, enabling only authorized entities to view specific information. This feature can be transformative in highly-regulated sectors like finance, where compliance requirements result in businesses collecting and storing troves of personally identifiable information on their users. By eliminating the need for maintaining and securing centralized databases, and by utilizing ZK proofs to meet regulatory requirements and ensuring data integrity, Midnight mitigates risks of phishing, corrupted databases, and social engineering attacks – as any unauthorized access would yield no useful information to potential attackers.
Concurrent Interaction with Smart Contracts
Midnight allows for concurrent interaction with smart contracts. This is done by dividing contract states in two parts: a public, on-chain state, and a local (or individual) state, which is not publicly available on the blockchain.
Contract parties use zk-SNARKs to create a proof of their state changes. These proofs are submitted to the blockchain as transactions. This effectively allows for concurrency, as different parties can interact with the state privately.
Mitigating Attacks - ZK Proofs
Using zero-knowledge proofs, off-chain state changes are validated and submitted as on-chain transactions, preventing malicious actors from exploiting intermediate states. This feature is particularly effective in scenarios like Radiant Capital and Sonne Finance, where attackers manipulated public states and execution sequences. Midnight’s support for transaction reordering further mitigates risks by resolving conflicts and reducing leakage of sensitive data during state transitions. By shielding the private state and securing the execution flow, Midnight ensures resilience against exploits such as flash loan attacks, oracle manipulation, and unauthorized privilege elevation.
The support for more private state interactions also allows for cookieless environments as users can be authorized using ZK proofs. Moreover, since Midnight manages state locally and transaction metadata is protected by the DUST shielded resource, the network can enable strong security and data protection properties to emerge.
Midnight Network - Looking Ahead
Midnight brings much-needed improvements to the broader Web3 space by enabling data protection and privacy-preserving features. The following are a few examples of how Midnight’s solutions may look like in action.
Tokenization of Real-World Assets
The secure and private handling of data is essential for the tokenization of real-world assets. Ownership details over these assets need to be validated and securely stored. This can be effectively and efficiently done with the help of ZK proofs and private state management.
Interoperability
Midnight uses an improved Halo2 framework that will allow for recursive proofs, and the BLS signature scheme, compatible with networks such as Cardano and Ethereum.
Enhanced Privacy for Enterprise Adoption
Enterprises are hesitant to adopt blockchain technology due to concerns over exposing sensitive operations, proprietary, or customer data. Midnight allows for privacy-preserving smart contracts and for sensitive information to be kept entirely off-chain, while allowing for complex workflows and transactions.
DID (Decentralized Identity)
Decentralized Identity is one of the most powerful use cases of Midnight and ZK proofs. Users can prove their identity without revealing private information. This essentially prevents users from many forms of surveillance and subsequent exploitation. By combining zero-knowledge and selective disclosure of data, Midnight would allow users to prove their identity without sharing more information than absolutely required.
Improved Governance Systems
Transparent on-chain voting can compromise privacy. Midnight’s architecture ensures confidentiality and accountability through cryptographic proofs, and can allow voters to cast their votes without revealing their preferences or holdings, reducing governance manipulation risks. For instance, DAOs can greatly benefit from this as it fosters fair decision-making while maintaining privacy.
Regulatory Compliance
Blockchain systems often face scrutiny from regulators due to their pseudonymous nature which can sometimes be used in the course of illicit activities. Midnight can enable businesses to prove adherence to AML (Anti-Money Laundering) or KYC (Know-Your-Customer) regulations without exposing sensitive data.
Data Protection Blockchain
The coexistence and interplay between on-chain and off-chain states enable a system where sensitive data can be protected and kept by users, and never revealed in the public blockchain.
Ease of Use
Midnight eases the work for developers as they can deploy applications using Compact, a Typescript-based domain-specific language with a familiar and smooth learning curve.
Conclusion: Addressing Privacy and Security Challenges
The events of 2024 underscore the need for more robust privacy and security solutions across both Web2 and Web3 ecosystems. From large-scale data breaches to targeted exploits on blockchain protocols, the overall trend clearly shows the need for improved technical safeguards.
Midnight presents a framework capable of addressing these challenges through features such as zero-knowledge proofs, metadata shielding, and selective disclosure. Its modular architecture allows smart contracts to interact with both private and public states, ensuring flexibility for developers while offering tools that enable builders to comply with regulations.
As digital infrastructure continues to evolve, protocols like Midnight offer a new paradigm with concrete solutions to recurring vulnerabilities, reducing exposure to common attack vectors while enabling more privacy-preserving applications.
The adoption of such approaches marks a step toward addressing systemic weaknesses in existing systems and establishing a more resilient foundation for secure digital interactions.
Disclaimer: The content of this article solely reflects the author's opinion and does not represent the platform in any capacity. This article is not intended to serve as a reference for making investment decisions.
You may also like
Bitget Incentive Program: Win up to 1,100 USDT Per Week
CandyBomb x MET: Trade futures to share 20,000 MET!
CandyBomb x MET: Trade futures to share 20,000 MET!
